It is possible to "chain” VPN servers so that your data is routed between two or more VPN servers as it travels between you and the internet. Such chaining can provide some security benefits, but will always result in a major loss of speed.
Your PC/device -> VPN server 1 -> VPN server 2 -> Internet
Chaining VPN servers is possible using either a VPN service that offers it as a feature, or you can do it yourself using a Virtual Machine (VM).
Double-hop VPN services
Some VPN services offer multihop VPN connections, allowing you to route your VPN connection through two or more of their servers. The most prominent of these are NordVPN and IVPN, but some smaller providers (which I am not familiar with) also offer this as a feature.
The advantage of chaining VPN servers in this way is that the VPN provider does all the hard work. It is usually simply a matter of selecting the correct profile in the VPN client, and everything else is taken care of automatically.
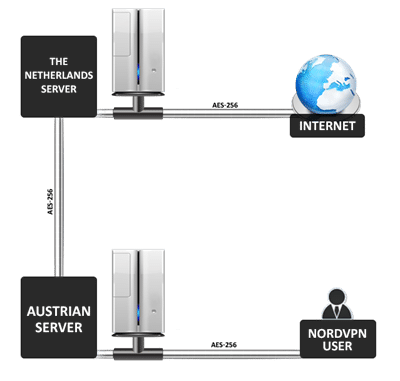
NordVPN only supports "Double VPN” through its Austria -> Netherlands servers. As you can see, data is re-encrypted as it leaves each server

IVPN, on the other hand, allows you to double-hop through any of its servers
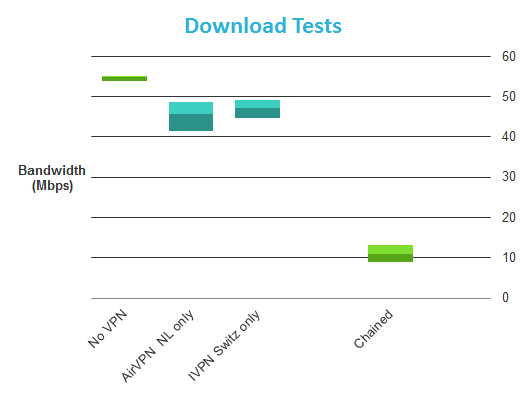
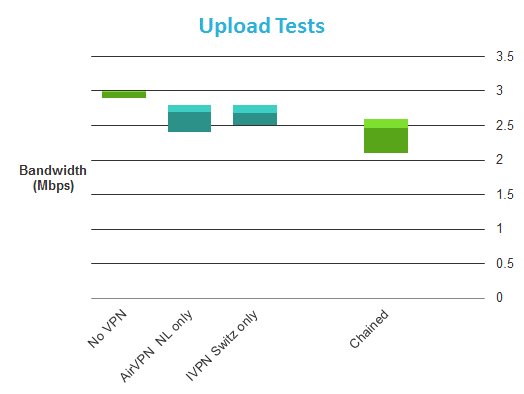
Aside from the fact that any extra hops will seriously slow down your internet connection (see our IVPN Review for some speed test results), I am very dubious about the value of such a setup. This is because the VPN provider still routes the signal, so:
a) Adversaries will be easily able to trace a user to that VPN service, and
b) The provider still does the routing, so it knows exactly who is connected to what, no matter how many servers your data is routed through.
Of course, if the provider keeps no logs, uses shared IP’s, etc., it may not be able to turn over any information, but this is exactly the same as if a single VPN server was being used!
If the VPN provider is not compromised, then multi-hopping through servers located in countries where an adversary has no leverage might help prevent it tracking a connection back to you. For example, if you are concerned about being traced by the NSA, double-hoping through servers located China and Russia might conceivably make life difficult for the NSA. However:
a) Very few providers actually offer servers located in such locations (and China bans all VPN services)
b) Can you really trust VPN servers located in such counties?
Chaining VPN servers yourself
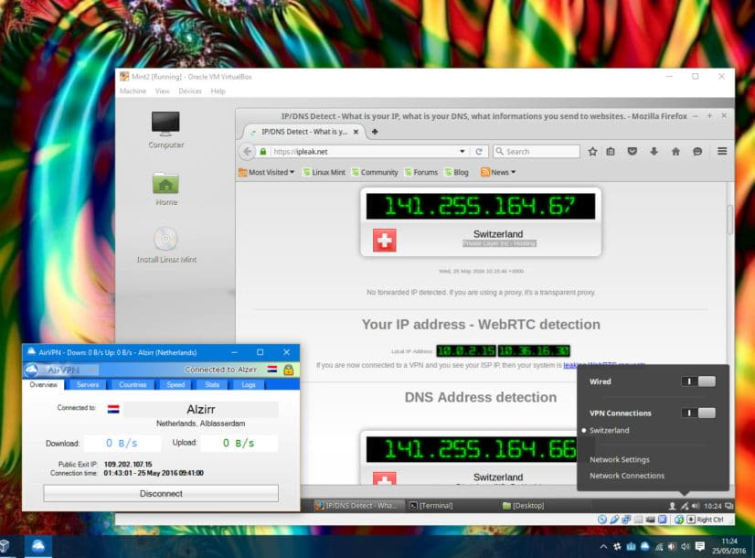
Another option is to chain VPN servers yourself using Virtual Machines. Virtual Machines effectively allow you run one Operating System (OS) inside another. It is therefore possible to connect to one VPN service using your primarily OS, and then connect to a second one from within the VM.
All connections from within the Virtual Machine will be routed through both VPN servers (with the one your primary OS is connected to being the first).
A 2 server chain using a Virtual Machines would, therefore, work something like this:
PC -> VPN 1 -> Virtual Machine -> VPN 2 -> Internet
The advantages of this over using a double-hop VPN service are:
- You are protected by 2 completely different VPN services, making it twice as difficult for an adversary to identify you. Note that this only really applies if you use privacy-friendly no logs providers
- You are completely free to decide which servers to connect to
- There is no limit to how many servers you can chain (except the power of your PC and how much of a speed hit you are willing to take).
Disadvantages include:
- You now need to trust two VPN services, rather than just one
- Can be pricey, as you need to pay for each VPN service you use (you could use free services, but this would lose many of the privacy advantages that chaining VPN servers brings. Most free services aren't trustworthy and in fact keep logs (or else have data and/or speed limits that would likely be crippling over a multihop connection)
- It is a pain to setup
- You will suffer the combined speed hit of connecting to every VPN server that you chain (at least!).
Example setup
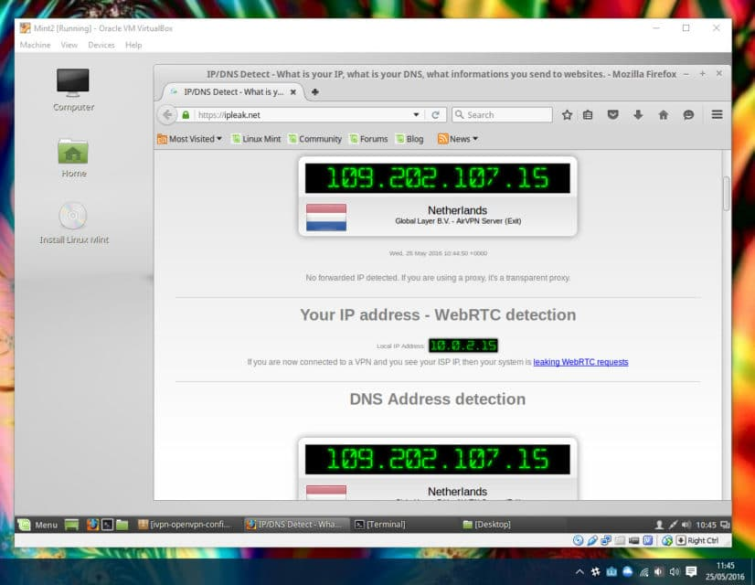
Below is an example setup for chaining VPN servers yourself, using a Windows 10 PC running Oracle VM VirtualBox. Please note that if you are serious about security, you should seriously consider using some version of Linux as your primary OS instead of Windows. The process for doing this in OSX or Linux is very similar.
- Download some VM software and an Operating System. For this example I have used VirtualBox (available for both Windows and OSX) to create a Virtual Machine, into which I loaded the Linux Mint OS. These are both free and open source.